Configuring VLANs in Cisco’s IOS
In the following I’m going to share one of my Cisco Packet Tracer practices. To memorize and practice some basic IOS commands I’ve created the network below for myself. Because I’ve saved every command I thought to share it on my blog since it might be helpful for someone.
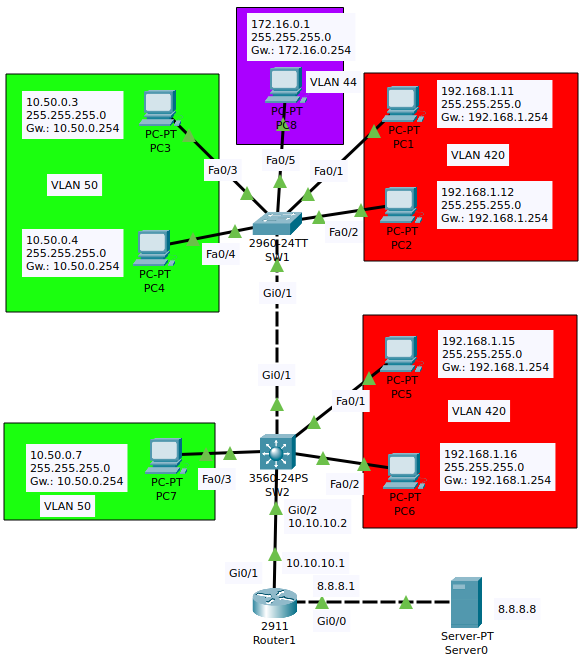
With the help of the Layer3 switch and SW2’s SVI interfaces I can perform inter-VLAN routing without the router. Let’s start with SW1: I changed the hostname, put the interfaces into access mode and added to VLANs (which have been created automatically). I defined Gi0/1 interface as a trunk port, enabled the VLANs on it and specified the native VLAN (it’ll be same for SW2 for security purposes).
Switch>
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#hostname SW1
SW1(config)#interface range Fa0/1 - 2
SW1(config-if-range)#switchport mode access
SW1(config-if-range)#switchport access vlan 420
% Access VLAN does not exist. Creating vlan 420
SW1(config-if-range)#vlan 420
SW1(config-vlan)#name RED
SW1(config-vlan)#exit
SW1(config)#interface range Fa0/3 - 4
SW1(config-if-range)#switchport mode access
SW1(config-if-range)#switchport access vlan 50
% Access VLAN does not exist. Creating vlan 50
SW1(config-if-range)#vlan 50
SW1(config-vlan)#name GREEN
SW1(config-vlan)#exit
SW1(config)#interface Fa0/5
SW1(config-if)#switchport mode access
SW1(config-if)#switchport access vlan 44
% Access VLAN does not exist. Creating vlan 44
SW1(config-if)#vlan 44
SW1(config-vlan)#name PURPLE
SW1(config-vlan)#exit
SW1(config)#show vlan brief
^
% Invalid input detected at '^' marker.
SW1(config)#do show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/6, Fa0/7, Fa0/8, Fa0/9
Fa0/10, Fa0/11, Fa0/12, Fa0/13
Fa0/14, Fa0/15, Fa0/16, Fa0/17
Fa0/18, Fa0/19, Fa0/20, Fa0/21
Fa0/22, Fa0/23, Fa0/24, Gig0/1
Gig0/2
44 PURPLE active Fa0/5
50 GREEN active Fa0/3, Fa0/4
420 RED active Fa0/1, Fa0/2
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
SW1(config)#interface Gi0/1
SW1(config-if)#switchport trunk encapsulation dot1q
^
% Invalid input detected at '^' marker.
SW1(config-if)#switchport mode trunk
SW1(config-if)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to down
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
SW1(config-if)#do show interfaces trunk
Port Mode Encapsulation Status Native vlan
Gig0/1 on 802.1q trunking 1
Port Vlans allowed on trunk
Gig0/1 1-1005
Port Vlans allowed and active in management domain
Gig0/1 1,44,50,420
Port Vlans in spanning tree forwarding state and not pruned
Gig0/1 none
SW1(config-if)#switchport trunk allowed vlan 50,420
SW1(config-if)#switchport trunk native vlan 69
SW1(config-if)#do show interfaces trunk
Port Mode Encapsulation Status Native vlan
Gig0/1 on 802.1q trunking 69
Port Vlans allowed on trunk
Gig0/1 50,420
Port Vlans allowed and active in management domain
Gig0/1 50,420
Port Vlans in spanning tree forwarding state and not pruned
Gig0/1 420Let’s continue with SW2’s configuration: I did the same for SW2. Ignore the native VLAN mismatch message, I defined that at the end of the block. Note that I haven’t specified VLAN 44 on this switch, so it won’t be allowed on the trunk port, I’ll do it later.
Switch>
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#hostname SW2L3
SW2L3(config)#interface range Fa0/1-2
SW2L3(config-if-range)#switchport mode access
SW2L3(config)#interface range Fa0/1-2
SW2L3(config-if-range)#switchport access vlan 420
% Access VLAN does not exist. Creating vlan 420
SW2L3(config-if-range)#vlan 420
SW2L3(config-vlan)#name
%CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on GigabitEthernet0/1 (1), with SW1 GigabitEthernet0/1 (69).
% Incomplete command.
SW2L3(config-vlan)#name RED
SW2L3(config-vlan)#
SW2L3(config-vlan)#exit
SW2L3(config)#interface Fa0/3
SW2L3(config-if)#switchport mode access
SW2L3(config-if)#switchport access vlan 50
% Access VLAN does not exist. Creating vlan 50
SW2L3(config-if)#vlan 50
SW2L3(config-vlan)#name G
%CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on GigabitEthernet0/1 (1), with SW1 GigabitEthernet0/1 (69).
R
SW2L3(config-vlan)#name GREEN
SW2L3(config-vlan)#exit
SW2L3(config)#do show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/4, Fa0/5, Fa0/6, Fa0/7
Fa0/8, Fa0/9, Fa0/10, Fa0/11
Fa0/12, Fa0/13, Fa0/14, Fa0/15
Fa0/16, Fa0/17, Fa0/18, Fa0/19
Fa0/20, Fa0/21, Fa0/22, Fa0/23
Fa0/24, Gig0/2
50 GREEN active Fa0/3
420 RED active Fa0/1, Fa0/2
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
SW2L3(config)#
SW2L3(config)#interface Gi0/1
SW2L3(config-if)#switchport mode trunk
Command rejected: An interface whose trunk encapsulation is "Auto" can not be configured to "trunk" mode.
SW2L3(config-if)#switchport trunk encapsulation dot1q
SW2L3(config-if)#switchport mode trunk
SW2L3(config-if)#switchport trunk native vlan 69
SW2L3(config-if)#switchport trunk allowed vlan 50,420
SW2L3(config-if)#
SW2L3(config-if)#exit
SW2L3(config)#do show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/4, Fa0/5, Fa0/6, Fa0/7
Fa0/8, Fa0/9, Fa0/10, Fa0/11
Fa0/12, Fa0/13, Fa0/14, Fa0/15
Fa0/16, Fa0/17, Fa0/18, Fa0/19
Fa0/20, Fa0/21, Fa0/22, Fa0/23
Fa0/24, Gig0/2
50 GREEN active Fa0/3
420 RED active Fa0/1, Fa0/2
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
SW2L3(config)#
SW2L3(config)#do show interfaces trunk
Port Mode Encapsulation Status Native vlan
Gig0/1 on 802.1q trunking 69
Port Vlans allowed on trunk
Gig0/1 50,420
Port Vlans allowed and active in management domain
Gig0/1 50,420
Port Vlans in spanning tree forwarding state and not pruned
Gig0/1 420
Next I enabled the IP routing on the Layer3 switch and created the SVIs which will be the default gateways for the hosts.
SW2L3(config)#ip routing
SW2L3(config)#interface vlan 50
SW2L3(config-if)#ip address 10.50.0.254 255.255.255.0
SW2L3(config-if)#no shutdown
SW2L3(config-if)#exit
SW2L3(config)#interface vlan 420
SW2L3(config-if)#ip address 192.168.1.254 255.255.255.0
SW2L3(config-if)#no shutdown
SW2L3(config-if)#exit
SW2L3(config)#do show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/1 unassigned YES unset up up
FastEthernet0/2 unassigned YES unset up up
FastEthernet0/3 unassigned YES unset up up
FastEthernet0/4 unassigned YES unset down down
FastEthernet0/5 unassigned YES unset down down
FastEthernet0/6 unassigned YES unset down down
FastEthernet0/7 unassigned YES unset down down
FastEthernet0/8 unassigned YES unset down down
FastEthernet0/9 unassigned YES unset down down
FastEthernet0/10 unassigned YES unset down down
FastEthernet0/11 unassigned YES unset down down
FastEthernet0/12 unassigned YES unset down down
FastEthernet0/13 unassigned YES unset down down
FastEthernet0/14 unassigned YES unset down down
FastEthernet0/15 unassigned YES unset down down
FastEthernet0/16 unassigned YES unset down down
FastEthernet0/17 unassigned YES unset down down
FastEthernet0/18 unassigned YES unset down down
FastEthernet0/19 unassigned YES unset down down
FastEthernet0/20 unassigned YES unset down down
FastEthernet0/21 unassigned YES unset down down
FastEthernet0/22 unassigned YES unset down down
FastEthernet0/23 unassigned YES unset down down
FastEthernet0/24 unassigned YES unset down down
GigabitEthernet0/1 unassigned YES unset up up
GigabitEthernet0/2 unassigned YES unset down down
Vlan1 unassigned YES unset administratively down down
Vlan50 10.50.0.254 YES manual up up
Vlan420 192.168.1.254 YES manual up upNow hosts in different VLANs should be able to ping each other. Instead of an ROAS configuration the Layer3 switch does the inter-VLAN routing.
I forgot defining VLAN 44 before, I do it on both SW1 and SW2:
SW1>enable
SW1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)#interface gi0/1
SW1(config-if)#switchport trunk allowed vlan add 44
SW1(config-if)#do show interfaces trunk
Port Mode Encapsulation Status Native vlan
Gig0/1 on 802.1q trunking 69
Port Vlans allowed on trunk
Gig0/1 44,50,420
Port Vlans allowed and active in management domain
Gig0/1 44,50,420
Port Vlans in spanning tree forwarding state and not pruned
Gig0/1 44,50,420SW2:
SW2L3(config)#
SW2L3(config)#vlan 44
SW2L3(config-vlan)#exit
SW2L3(config)#vlan 44
SW2L3(config-vlan)#name PURPLE
SW2L3(config-vlan)#exit
SW2L3(config)#interface Gi0/1
SW2L3(config-if)#switchport trunk allowed vlan add 44
SW2L3(config-if)#do show interfaces trunk
Port Mode Encapsulation Status Native vlan
Gig0/1 on 802.1q trunking 69
Port Vlans allowed on trunk
Gig0/1 44,50,420
Port Vlans allowed and active in management domain
Gig0/1 44,50,420
Port Vlans in spanning tree forwarding state and not pruned
Gig0/1 44,50,420
SW2L3(config)#interface vlan 44
SW2L3(config-if)#
%LINK-5-CHANGED: Interface Vlan44, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan44, changed state to up
SW2L3(config-if)#ip address 172.16.0.254 255.255.255.0
SW2L3(config-if)#no shutdown
SW2L3(config-if)#exit
SW2L3(config)#do show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/1 unassigned YES unset up up
FastEthernet0/2 unassigned YES unset up up
FastEthernet0/3 unassigned YES unset up up
FastEthernet0/4 unassigned YES unset down down
FastEthernet0/5 unassigned YES unset down down
FastEthernet0/6 unassigned YES unset down down
FastEthernet0/7 unassigned YES unset down down
FastEthernet0/8 unassigned YES unset down down
FastEthernet0/9 unassigned YES unset down down
FastEthernet0/10 unassigned YES unset down down
FastEthernet0/11 unassigned YES unset down down
FastEthernet0/12 unassigned YES unset down down
FastEthernet0/13 unassigned YES unset down down
FastEthernet0/14 unassigned YES unset down down
FastEthernet0/15 unassigned YES unset down down
FastEthernet0/16 unassigned YES unset down down
FastEthernet0/17 unassigned YES unset down down
FastEthernet0/18 unassigned YES unset down down
FastEthernet0/19 unassigned YES unset down down
FastEthernet0/20 unassigned YES unset down down
FastEthernet0/21 unassigned YES unset down down
FastEthernet0/22 unassigned YES unset down down
FastEthernet0/23 unassigned YES unset down down
FastEthernet0/24 unassigned YES unset down down
GigabitEthernet0/1 unassigned YES unset up up
GigabitEthernet0/2 unassigned YES unset down down
Vlan1 unassigned YES unset administratively down down
Vlan44 172.16.0.254 YES manual up up
Vlan50 10.50.0.254 YES manual up up
Vlan420 192.168.1.254 YES manual up upNow PC8 should be able to ping every other hosts as well.
With the help of Router1 and specifying default gateways for both R1 and SW2 an external server will be available for every host, the commands on SW2 and R1 are the following:
Router>
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#interface gi0/0
Router(config-if)#no shutdown
Router(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up
Router(config-if)#
Router(config-if)#exit
Router(config)#interface gi0/1
Router(config-if)#no shutdown
Router(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
Router(config-if)#exit
Router(config)#interface gi0/0
Router(config-if)#ip address 8.8.8.1 255.255.255.0
Router(config-if)#exit
Router(config)#do show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 8.8.8.1 YES manual up up
GigabitEthernet0/1 unassigned YES unset up up
GigabitEthernet0/2 unassigned YES unset administratively down down
Vlan1 unassigned YES unset administratively down down
Router(config)#interface g0/1
Router(config-if)#ip address 10.10.10.1 255.255.255.0
Router(config-if)#no shutdown
Router(config-if)#do show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 8.8.8.1 YES manual up up
GigabitEthernet0/1 10.10.10.1 YES manual up up
GigabitEthernet0/2 unassigned YES unset administratively down down
Vlan1 unassigned YES unset administratively down down
Router(config)#ip route 0.0.0.0 0.0.0.0 10.10.10.2
SW2L3#
SW2L3#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
SW2L3(config)#interface Gi0/2
SW2L3(config-if)#no switchport
SW2L3(config-if)#ip address 10.10.10.2 255.255.255.0
SW2L3(config-if)#ip route 0.0.0.0 0.0.0.0 10.10.10.1
SW2L3(config)#do show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/1 unassigned YES unset up up
FastEthernet0/2 unassigned YES unset up up
FastEthernet0/3 unassigned YES unset up up
FastEthernet0/4 unassigned YES unset down down
FastEthernet0/5 unassigned YES unset down down
FastEthernet0/6 unassigned YES unset down down
FastEthernet0/7 unassigned YES unset down down
FastEthernet0/8 unassigned YES unset down down
FastEthernet0/9 unassigned YES unset down down
FastEthernet0/10 unassigned YES unset down down
FastEthernet0/11 unassigned YES unset down down
FastEthernet0/12 unassigned YES unset down down
FastEthernet0/13 unassigned YES unset down down
FastEthernet0/14 unassigned YES unset down down
FastEthernet0/15 unassigned YES unset down down
FastEthernet0/16 unassigned YES unset down down
FastEthernet0/17 unassigned YES unset down down
FastEthernet0/18 unassigned YES unset down down
FastEthernet0/19 unassigned YES unset down down
FastEthernet0/20 unassigned YES unset down down
FastEthernet0/21 unassigned YES unset down down
FastEthernet0/22 unassigned YES unset down down
FastEthernet0/23 unassigned YES unset down down
FastEthernet0/24 unassigned YES unset down down
GigabitEthernet0/1 unassigned YES unset up up
GigabitEthernet0/2 10.10.10.2 YES manual up up
Vlan1 unassigned YES unset administratively down down
Vlan44 172.16.0.254 YES manual up up
Vlan50 10.50.0.254 YES manual up up
Vlan420 192.168.1.254 YES manual up up
SW2L3(config)#do show ip route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 10.10.10.1 to network 0.0.0.0
10.0.0.0/24 is subnetted, 2 subnets
C 10.10.10.0 is directly connected, GigabitEthernet0/2
C 10.50.0.0 is directly connected, Vlan50
172.16.0.0/24 is subnetted, 1 subnets
C 172.16.0.0 is directly connected, Vlan44
C 192.168.1.0/24 is directly connected, Vlan420
S* 0.0.0.0/0 [1/0] via 10.10.10.1
Now every host can ping Google DNS (8.8.8.8), note that the TTL (Time to Live) value has been reduced by 2, since we have 2 routers between the hosts and the server:
C:\>ping 8.8.8.8
Pinging 8.8.8.8 with 32 bytes of data:
Reply from 8.8.8.8: bytes=32 time<1ms TTL=126
Reply from 8.8.8.8: bytes=32 time<1ms TTL=126
Reply from 8.8.8.8: bytes=32 time<1ms TTL=126
Reply from 8.8.8.8: bytes=32 time<1ms TTL=126
Ping statistics for 8.8.8.8:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms