Different NAT configurations on Cisco’s IOS
Recently I’ve made some Packet Tracer practices, I’m going to share the commands I’ve issued on Cisco routers, and describe the configuration of different type of source NATs.
1. Static Source NAT
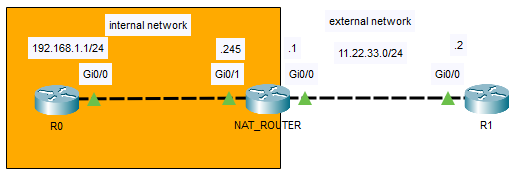
In this configurations we can translate one host’s private IP address (from the 10.0.0.0/8; 172.16.0.0/12 or from the 192.168.0.0/16 subnet) to a public IP address (in this case 11.22.33.44 to make it simple), let’s see the configuration:
NAT_ROUTER(config)#do show ip nat translations
NAT_ROUTER(config)#interface g0/1
NAT_ROUTER(config-if)#ip nat inside
NAT_ROUTER(config-if)#exit
NAT_ROUTER(config)#interface gi0/0
NAT_ROUTER(config-if)#ip nat outside
NAT_ROUTER(config-if)#exit
NAT_ROUTER(config)#ip nat inside source static 192.168.1.1 11.22.33.44
NAT_ROUTER(config)#end
NAT_ROUTER#
%SYS-5-CONFIG_I: Configured from console by console
NAT_ROUTER#show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 11.22.33.44 192.168.1.1 --- ---R0 and R1 can be replaced with a PC, I just chose router to practice the commands, so I set the default gateway and pinged R1 from R0:
R0(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.245
R0(config)#do ping 11.22.33.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 11.22.33.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 73/91/98 msLet’s see the NAT statistic:
NAT_ROUTER#show ip nat statistics
Total translations: 16 (1 static, 15 dynamic, 15 extended)
Outside Interfaces: GigabitEthernet0/0
Inside Interfaces: GigabitEthernet0/1
Hits: 27 Misses: 29
Expired translations: 14
Dynamic mappings:So it seems NAT is working properly. I started an IP packet debug on R1: R1 receives packets from 11.22.33.44 (R0’s public IP address), it doesn’t know R0’s private address:
R1#debug ip packet
Packet debugging is on
R1#
IP: tableid=0, s=11.22.33.44 (GigabitEthernet0/0), d=11.22.33.2 (GigabitEthernet0/0), routed via RIB
IP: s=11.22.33.44 (GigabitEthernet0/0), d=11.22.33.2 (GigabitEthernet0/0), len 128, rcvd 3
IP: tableid=0, s=11.22.33.2 (local), d=11.22.33.44 (GigabitEthernet0/0), routed via RIB
IP: s=11.22.33.2 (local), d=11.22.33.44 (GigabitEthernet0/0), len 128, sending2. Dynamic Source NAT
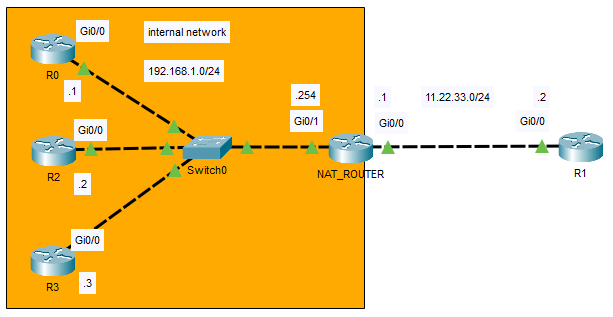
Dynamic NAT is not so different from static NAT: we crate a pool of public IP addresses, from which we assign IP addresses to hosts. It’s wasteful: we need a public address for each host in the private subnet.
NAT_ROUTER(config)#interface g0/0
NAT_ROUTER(config-if)#ip nat outside
NAT_ROUTER(config-if)#exit
NAT_ROUTER(config)#interface g0/1
NAT_ROUTER(config-if)#ip nat inside
NAT_ROUTER(config-if)#exit
NAT_ROUTER(config)#access-list 1 permit 192.168.1.0 0.0.0.255
NAT_ROUTER(config)#ip nat pool NAT_POOL_NAME 11.22.33.44 11.22.33.50 netmask 255.255.255.0
NAT_ROUTER(config)#ip nat inside source list 1 pool NAT_POOL_NAME
NAT_ROUTER(config)#do show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 11.22.33.44:2 192.168.1.1:2 11.22.33.2:2 11.22.33.2:2
icmp 11.22.33.44:3 192.168.1.1:3 11.22.33.2:3 11.22.33.2:3
icmp 11.22.33.44:4 192.168.1.1:4 11.22.33.2:4 11.22.33.2:4
icmp 11.22.33.44:5 192.168.1.1:5 11.22.33.2:5 11.22.33.2:5
icmp 11.22.33.45:2 192.168.1.2:2 11.22.33.2:2 11.22.33.2:2
icmp 11.22.33.45:3 192.168.1.2:3 11.22.33.2:3 11.22.33.2:3
icmp 11.22.33.45:4 192.168.1.2:4 11.22.33.2:4 11.22.33.2:4
icmp 11.22.33.45:5 192.168.1.2:5 11.22.33.2:5 11.22.33.2:5
icmp 11.22.33.46:2 192.168.1.3:2 11.22.33.2:2 11.22.33.2:2
icmp 11.22.33.46:3 192.168.1.3:3 11.22.33.2:3 11.22.33.2:3
icmp 11.22.33.46:4 192.168.1.3:4 11.22.33.2:4 11.22.33.2:4
icmp 11.22.33.46:5 192.168.1.3:5 11.22.33.2:5 11.22.33.2:5I started a NAT debug on the NAT_ROUTER: we can see how the private addresses are being translated:
NAT_ROUTER#debug ip nat
IP NAT debugging is on
NAT_ROUTER#
NAT: s=192.168.1.1->11.22.33.46, d=11.22.33.2 [6]
NAT*: s=11.22.33.2, d=11.22.33.46->192.168.1.1 [12]
NAT: s=192.168.1.1->11.22.33.46, d=11.22.33.2 [7]
NAT*: s=11.22.33.2, d=11.22.33.46->192.168.1.1 [13]
NAT: s=192.168.1.1->11.22.33.46, d=11.22.33.2 [8]
NAT*: s=11.22.33.2, d=11.22.33.46->192.168.1.1 [14]
NAT: s=192.168.1.1->11.22.33.46, d=11.22.33.2 [9]
NAT*: s=11.22.33.2, d=11.22.33.46->192.168.1.1 [15]
NAT: s=192.168.1.1->11.22.33.46, d=11.22.33.2 [10]
NAT*: s=11.22.33.2, d=11.22.33.46->192.168.1.1 [16]3. NAT Overloading – PAT
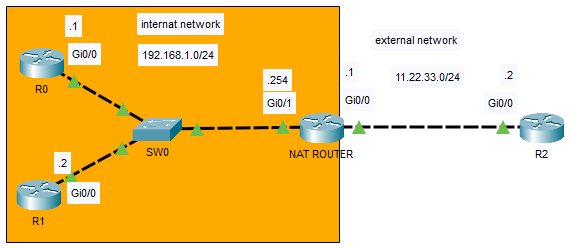
Configuring PAT (or NAT overloading) we can assign a single public IP address to multiple private IP addresses, the hosts with private IP are distinguished by port numbers.
NAT_ROUTER#show ip nat translations
NAT_ROUTER#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
NAT_ROUTER(config)#interface gi0/0
NAT_ROUTER(config-if)#ip nat outside
NAT_ROUTER(config-if)#exit
NAT_ROUTER(config)#interface gi0/1
NAT_ROUTER(config-if)#ip nat inside
NAT_ROUTER(config-if)#exit
NAT_ROUTER(config)#ip nat inside source list 1 interface g0/0
NAT_ROUTER(config)#access-list 1 permit 192.168.1.0 0.0.0.255PAT is not wasteful: we only need one public IP for multiple hosts. I started an SSH session with R0 and R1 to R2. The two hosts have the same Inside global address, but they use a different port number:
NAT_ROUTER#show ip nat translations
Pro Inside global Inside local Outside local Outside global
tcp 11.22.33.1:1030 192.168.1.1:1030 11.22.33.2:22 11.22.33.2:22
tcp 11.22.33.1:1032 192.168.1.2:1032 11.22.33.2:22 11.22.33.2:22